













Your external attack surface is constantly evolving, creating new risks from unknown assets, exposed services and misconfigurations. Below, we answer common questions about External Attack Surface Management and how DarkInvader helps security teams discover, monitor and prioritise external threats. If you need further clarity or a tailored demonstration, our team is here to help.
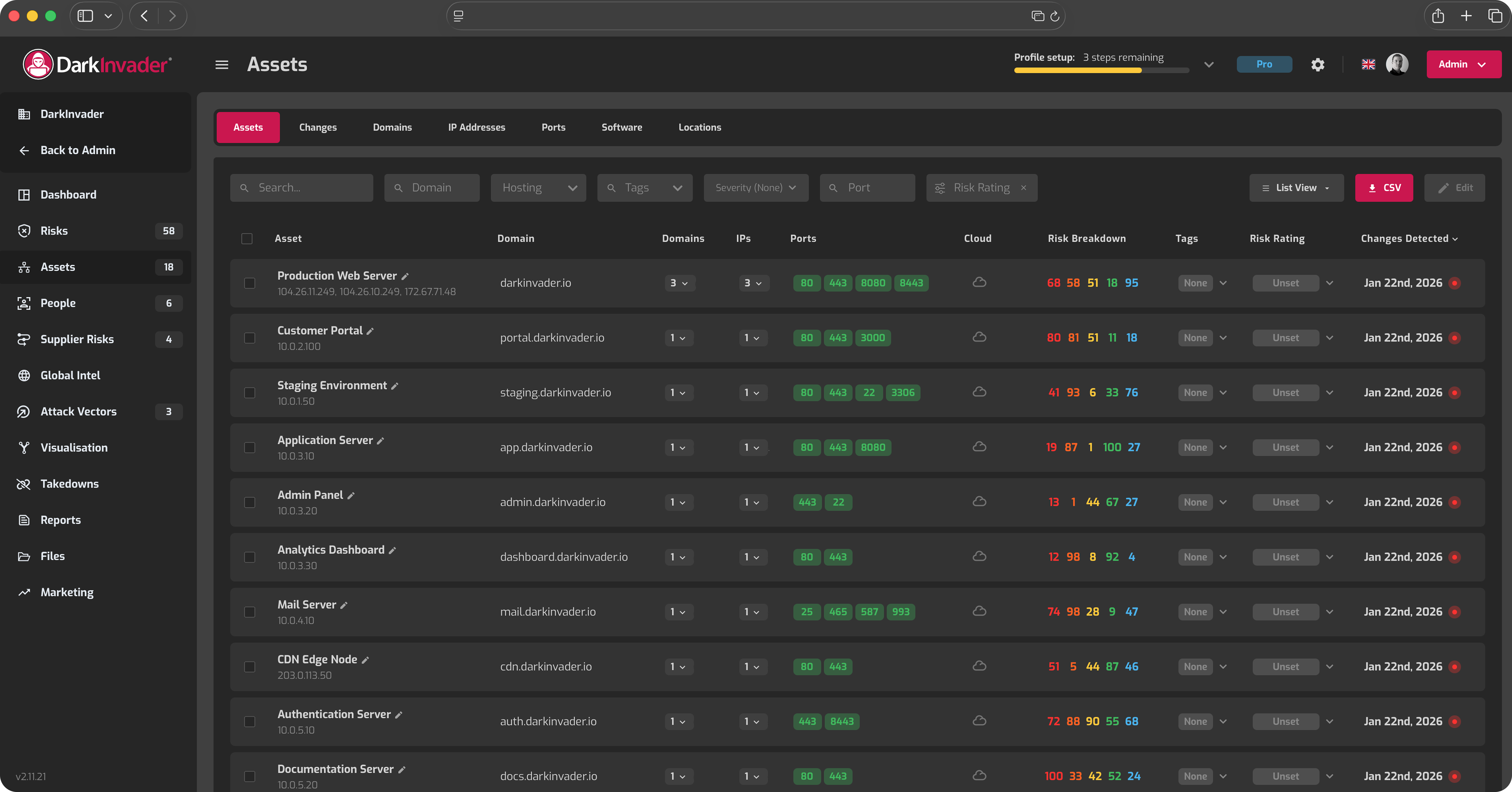
DarkInvader’s asset discovery automatically identifies all internet-facing assets associated with your organisation. This includes domains, subdomains, IP addresses, cloud infrastructure and exposed services. By building a continuously updated inventory of what is publicly reachable, DarkInvader ensures you have full visibility of your external footprint before attackers do.
Unknown or unmanaged assets, such as shadow IT, legacy systems or forgotten cloud instances, often lack proper security controls and monitoring. These blind spots expand your attack surface and create opportunities for exploitation. Identifying and managing these assets is critical to reducing breach risk.
DarkInvader presents discovered assets through a clear visual mapping interface, showing how domains, infrastructure and services are connected. This contextual view allows security teams to quickly understand exposure, identify high-risk areas and prioritise remediation efforts effectively.
Yes. DarkInvader’s automated discovery process is designed to uncover hidden, unauthorised or previously unknown assets linked to your organisation. By bringing these assets into visibility, your team can assess risk and apply appropriate security controls before they become entry points for attackers.
DarkInvader provides insight into where your internet-facing assets are hosted, including cloud providers and geographic locations. This helps organisations assess jurisdictional risk, third-party exposure and compliance considerations as part of broader security governance.
Unlock full visibility of your external attack surface with DarkInvader’s continuous, real-time monitoring. Create your free account to discover unknown assets, detect emerging risks and stay ahead of potential threats before attackers can exploit them.
Create My Free Account